In this tutorial we will describe how to protect simple PowerBuilder application (official site http://www.sybase.com/) against cracking, reverse engineering, disassembling and also we will embed such protection feature as licensing with software protection system Enigma Protector. We recommend to read this tutorial fully and apply all protection settings described there.
PowerBuilder applications are specific enough, there are specifics not only how the execution is organized, but also specifics in the files format. The ability to protect such files had been added since version Enigma Protector 3.160, older versions do not work with such kind of files. For testing, we recommend to download the latest available DEMO version from the official site Enigma Protector – Downloads
We will use Virtual Box as the main protection feature, it allows to emulate files in memory without having them on the disk.
The test program and patcher tool can be downloaded there: PowerBuilder Test and Patcher
Basic protection of PowerBuilder executable files
As we already said, the PowerBuilder executable files are very specific and require specific protection options. If you try to protect its exe without additional options – it will just fail. The reason of the fail – overlay data appended to the end of the exe file (overlay is a data that is not being mapped to the process memory). PowerBuilder file reads overlay to perform the execution. Overlay data contains a lot of structures with absolute file offsets, after protection the size of the file changes, absolute position of the overlay also changes and it becomes invalid, that’s because the protected file does not work.
To avoid this problem, we may use Virtual Box feature and put the original exe file in to %DEFAULT FOLDER% (so when the protected file will read overlay, it will read it from virtual file, which contains correct overlay because it is original file, and not from the protected one, which overlay becomes damaged after protection).
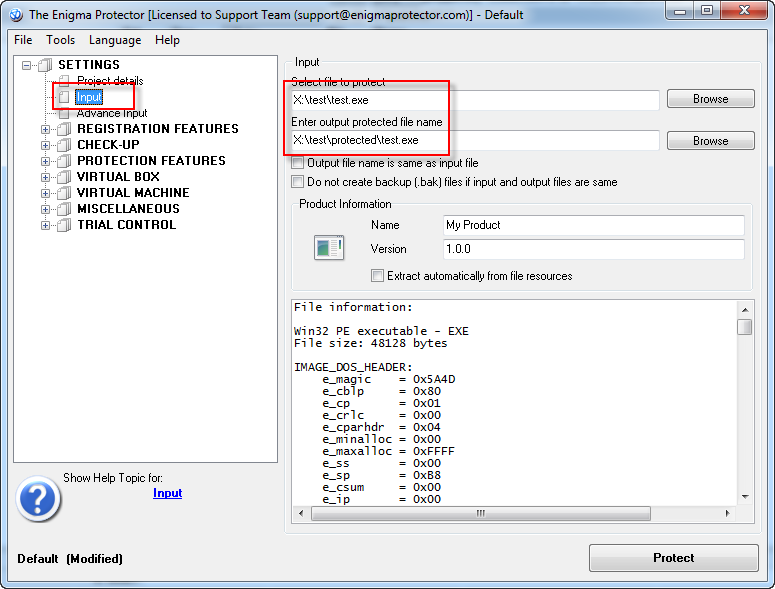
Run Enigma Protector, go to Input panel and select the input (file to protect) and output (protected) files. The major note at this step is that names of the input and output files have to be same!
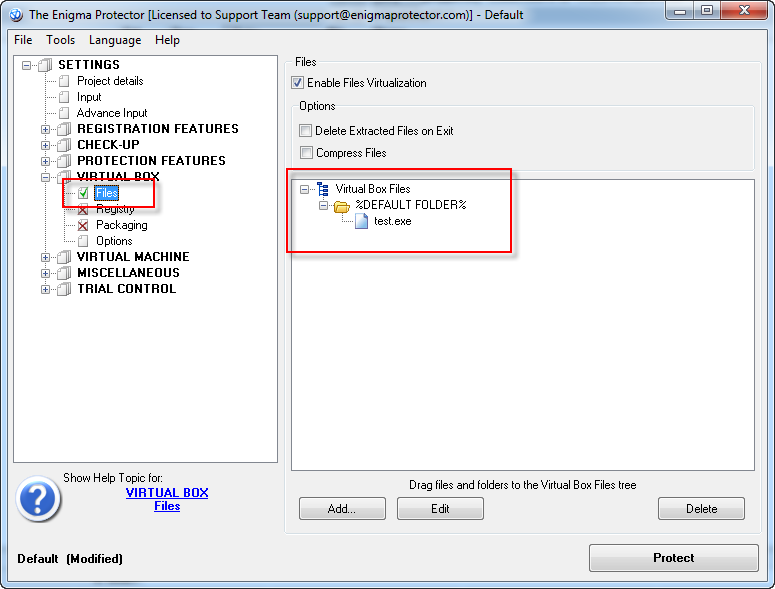
Then go to Virtual Box – Files panel and add the input file to the %DEFAULT FOLDER%
Try to protect the file now and run it. It will work. We may stop at this step, but this method has one major disadvantage – the original file is placed in Virtual Box and thus can be extracted.
Advanced protection of PowerBuilder executable file
As we said, having original exe file in Virtual Box is a vulnerability. We need this file in Virtual Box only due to it’s overlay data, we do not need it’s code and so on. So we may just delete all code from the file in Virtual Box to avoid the vulnerability.
This archive PowerBuilder Test and Patcher contains an utility that we called patcher, it deletes all code from the executable file and keeps only file overlay. We should use this utility for a file which we put in Virtual Box. Copy our input file test.exe to some temporary file, eg test_vb.exe. Then open the utility patcher\pbpatcherg32.exe from archive. Select the file copy there and click Patch button. If utility succeeded, the information message will be shown.
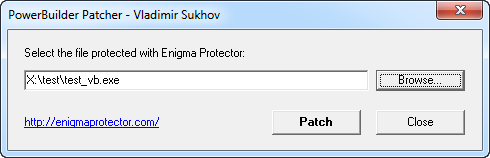
The console version of the patcher utility is also included in the archive.
Now switch to Enigma Protector, go to Virtual Box – Files panel, and delete the original test.exe we added there. Add our patched test_vb.exe now. Double click on the file to edit it’s properties. Change the file Virtual Path, so it will be named same as input file – test.exe
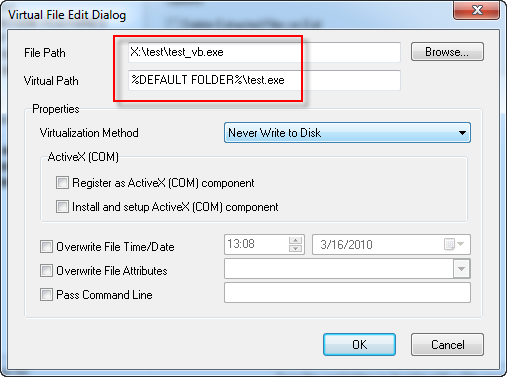
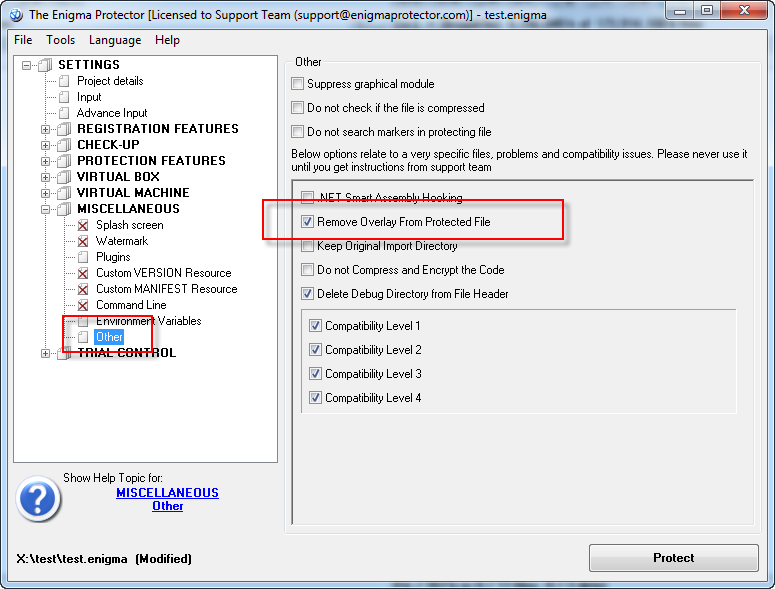
Since we read overlay data from the virtual file, we do not need an overlay in the original file anymore. To remove overlay from the protected file use the option Miscellaneous – Other – Remove Overlay from Protected File
Now protect the file, it also has to work, and it does not have the vulnerability we talked about.
Hiding PowerBuilder runtime files
PowerBuilder executables are not standalone programs and require a dozen additional dll files to run. These dll files can be custom libraries, or standard PowerBuilder runtimes. Standard libraries is an another weak point for protection, as the cracker may determine the type of application and choose the method to reverse it. With help of Virtual Box feature we may also hide and protect runtime library files too. Add the dll files in Virtual Box – Files, in to %DEFAULT FOLDER%. The option “Compress Files” also can be checked to reduce the size of the protected executable.
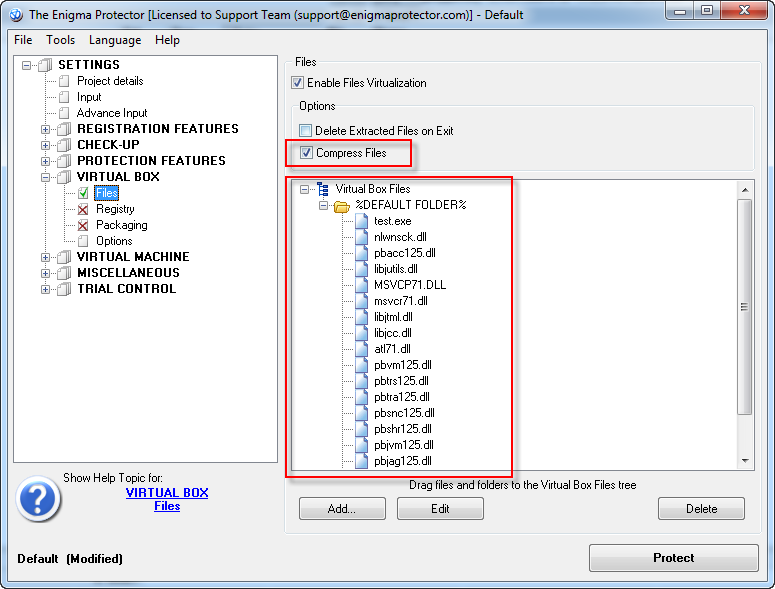
Moreover, we do not only hide the runtime libraries of our executable, we made a portable version of the application that consists from only one executable file, which does not require any other dll to run.
Add Licensing features
To show what also features of Enigma Protector we may apply, there are steps to add the licensing feature (ability to register the application with the license key).
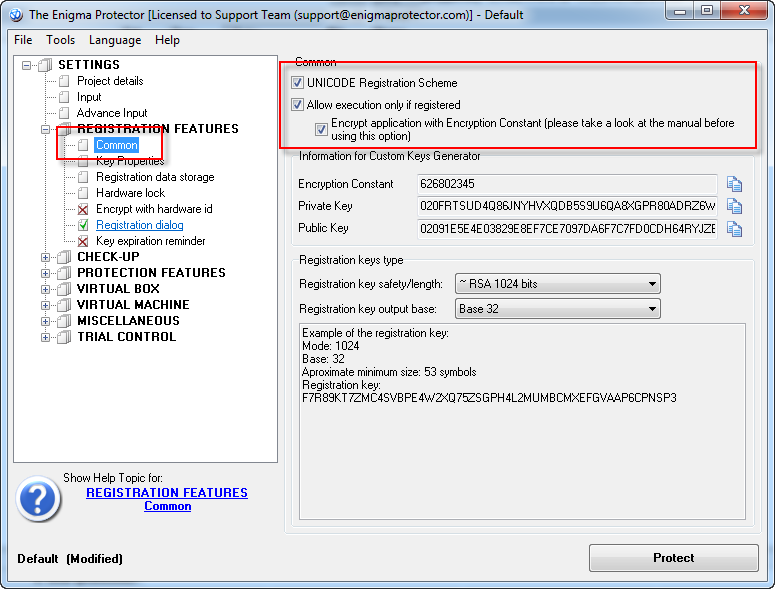
Specify the settings for registration:
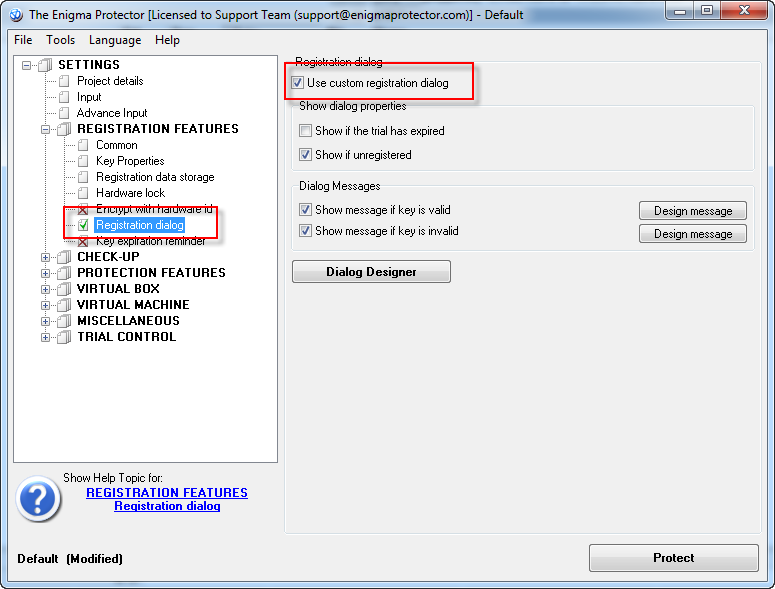
Enable standard registration dialog:
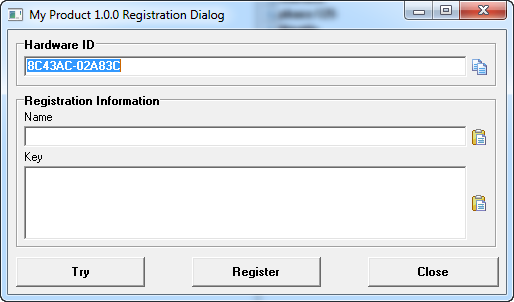
Try to protect the file. After you run it, the following registration dialog appears. It asks to enter the user name and key to continue execution. Without the license key our software won’t run.
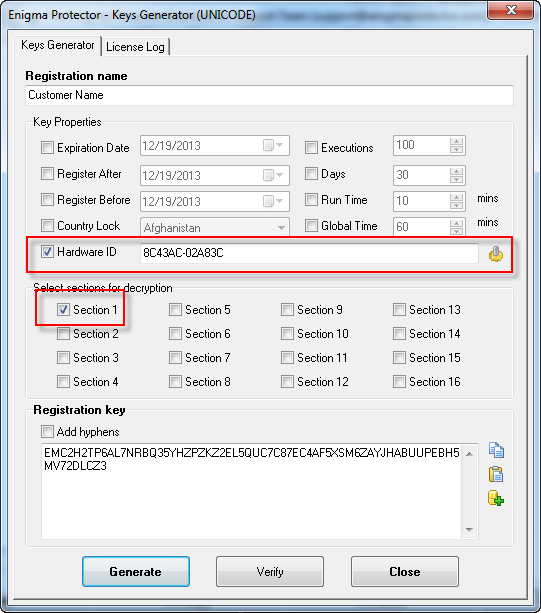
To generate a key, open the project in Enigma Protector, go to main menu – Tools – Keys Generator, and enter settings like this:
Hardware ID can be used only to lock the license key to a particular computer.
Enter the generated key and name into regisration dialog and register to continue execution.
Packing PowerBuilder files with Enigma Virtual Box
There is a freeware alternative to Enigma Protector that allows to merge PowerBuilder runtime libraries into single execution only.
To use Enigma Virtual Box, all steps up to Hiding PowerBuilder runtime files should be repeated. Note, Enigma Virtual Box can be used to pack all files into one executable, it does not provide the files protection as Enigma Protector does.