This article describes how to use Virtual Box functionality that is available in our commercial solution Enigma Protector and freeware Enigma Virtual Box. How to make application portable and hide files from users.
Virtual Box
This is a function that allows to merge files (and registry keys) into single protected/packed executable such way that application can still see these files (registry keys) but they won’t exist on the disk (registry). Protection emulates files (registry) calls in memory that helps to hide files (registry) from application user.
What is portable?
Portable program is the program that does not require installation, does not usually require administrator privileges and does not keep files (registry keys) on the user computer while using.
Most people prefer to use such programs because:
- No installation is required. Usually installers require administrator privileges to setup files on user computer, specially into Program Files folder which is write allowed for administrator users only. Running program with administrator privileges may cause vulnerabilities, like hard virus injection (if installer file is infected), unnecessary system configuration that comes from 3rd components or installer (eg, installation of unnecessary related products) and others;
- Portable application usually contains from a single executable file which is easy to deploy to USB stick and run wherever user wants;
- No trash files on user computer after program usage;
- Quick and full program removal.
How to use?
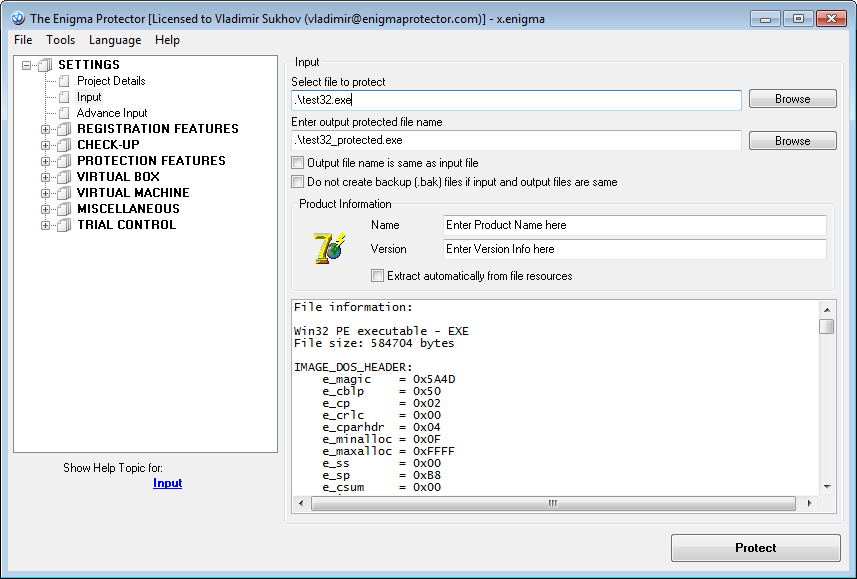
That’s rather simple, no special knowledge are required. Imagine, that your application contains from multiple files, it is usually a main executable file, some set of dll files, some images and data files. You need to:
- Select the main executable as a file to protect/pack. This file is a core for virtual system and it will contain all virtual files (registry keys) inside after protection
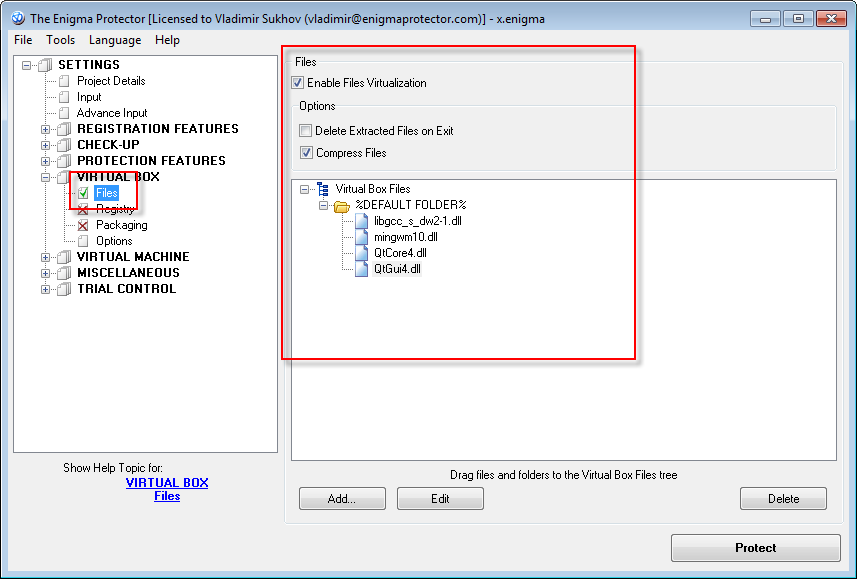
- Add files you would like to merge into Virtual Box – Files tree
- Protect/pack the file.
To repeat, the main goal of Virtual Box feature is that you do not need to have files you embedded there on the disk, after protection. Do not distribute embedded files together with protected application, it does not need/use them at all.
Frequent Mistakes and Limitations
Based on our experience, there is a list of most often happened issues and mistakes, when using Virtual Box feature:
- Incorrect location of virtual files in the tree. Many users think that if program is installed into Program Files folder, then the root folder in the files tree should also be Program Files. No, that’s wrong! This does not matter for program and for Virtual Box where the program is currently located and where it installs. What matters there is a location of embedded files relative to the main executable. For example: if a dll (which you would like to merge) is located in the same folder with main executable, then it should be added to %DEFAULT FOLDER% of files tree (%DEFAULT FOLDER% means the folder of main executable). If dll is located in the “data” subfolder of the folder with main executable, then in Virtual Box you have to add a root %DEFAULT FOLDER%, then add a subfolder “data” and then add a dll into that.
- Another executable files can also be added to Virtual Box, it’s OK. But Virtual Box will be able to run the virtual exe file only if architectures of main executable and virtual are the same, i.e. both files are 32 bit or 64 bit executables. If main executable is 32 bit file, but virtual is 64 bit, then Virtual Box will be unable to start such virtual exe.
Enigma Protector vs Enigma Virtual Box
What are the difference between these two softwares? First of all, both of them has the function Virtual Box and you should use ONLY ONE OF THEM, do not try to combine these programs, this is does not make sense! Apart of that, Enigma Protector provides a set of valuable benefits:
- A wide range of protection features (anti-cracking, anti-reverse engineering, anti-debugging, anti-dumping and so on), application licensing etc;
- Data encryption, the content of virtual files is encrypted inside protected file (apart of Enigma Virtual Box, the content is not hidden);
- Files protection, application calls to protected files are secured, to avoid being extracted and reused.
If you need even a basic protection for embedded files, we recommend to use Enigma Protector only.
