Xojo (Formerly known as Real Basic) is easy to use Rapid IDE which is using enhanced BASIC as the main language to develop. Compiled Xojo executable file is using a set of libraries (aka Xojo runtime) which are required for application to work. Xojo developers have to distribute these libraries together with application in order to work application properly. For today, Xojo does not allow to link/embed runtime libraries into single executable, so apart of protection, in this article we explain how to force this runtime to be merged with executable (for easier and compact application distribution).
Here we explain how to use Enigma Protector for:
- Application Protection. Enigma Protector has a lot of functions to protect the file against cracking, reverse engineering, debugging, running under virtual machine and so on;
- Application Licensing. With help of Enigma Protectior you could embed a licensing and trial features for your application to prepare it for selling or limit it usage to particular computers;
- Merge Xojo runtime libraries to single executable. We will use Virtual Box feature of Enigma Protector. This is the unique and very powertful feature that allows to hide files by emulating them in memory only, no files are being extracted to the disk!
- Use Enigma API functions for communication with protection from Xojo application.
Contents:
- Basic protection of Xojo executable & Runtime files
- Merge Xojo runtime to single executable (aka, Advanced protection of Xojo files)
- Common Protection Settings
- Licensing settings
- Trial settings for Xojo Application
- Registering the Application
Download the example 32Bit-Xojo-Enigma-API-v1.0 themed as “Application test & Xojo Engima Api”. Please note, in this example we are using special Enigma API functions, these functions start to work only after protection! Until the file is not protected, Enigma API functions won’t work.
Compile or Build the “enigma_ide_32bit-Unicode.xojo_xml_project” as Windows x86 or 32 Bit Application with Xojo. Let’s assume our project is located in “I:\Xojo\Enigma\Untitled” for futher references.
Basic protection of Xojo executable & Runtime files
As we already said, Xojo executable files are very specific and require specific protection options. However, we have noticed that there are 2 different types of Xojo applications (unfortunately, do not know the specifics of how to make 1st or 2nd type of files, let’s jsut describe both):
- No additional protection settings are required, protected file begins to work with default protection settings
- Overlayed executable (most frequently happens), if you protect such file with default protection options and run it, it will hang with the following error
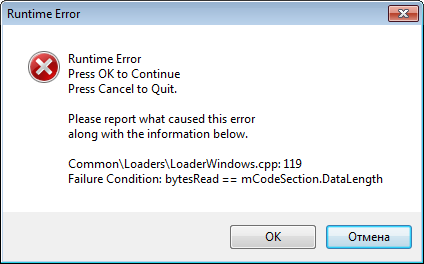
If #1 works for you, please skip the below recommenation. Do that only if #2 happens!
The reason of that fail – overlay data, which is the specific data that Xojo appends to the end of exe file. Since overlay data contains a lot of structures with absolute file offsets, after protection the size of the file changes and Xojo runtime is unable to find and read overlay data. Btw, would be good that Xojo developers someday fix this problem and make their files more flexible for such kind of protection.
To avoid this problem, we should use Virtual Box feature of Enigma Protector and put the original exe file in to %DEFAULT FOLDER% (so when the protected file will read overlay, it will read it from virtual file, which contains correct overlay because it is original file, and not from the protected one, which overlay becomes damaged after protection).
Run Enigma Protector, create a new project (which is very important) or open an existing one, go to Input panel and select the input (file to protect) and output (protected) files. The major note at this step is that names of the input and output files have to be same!
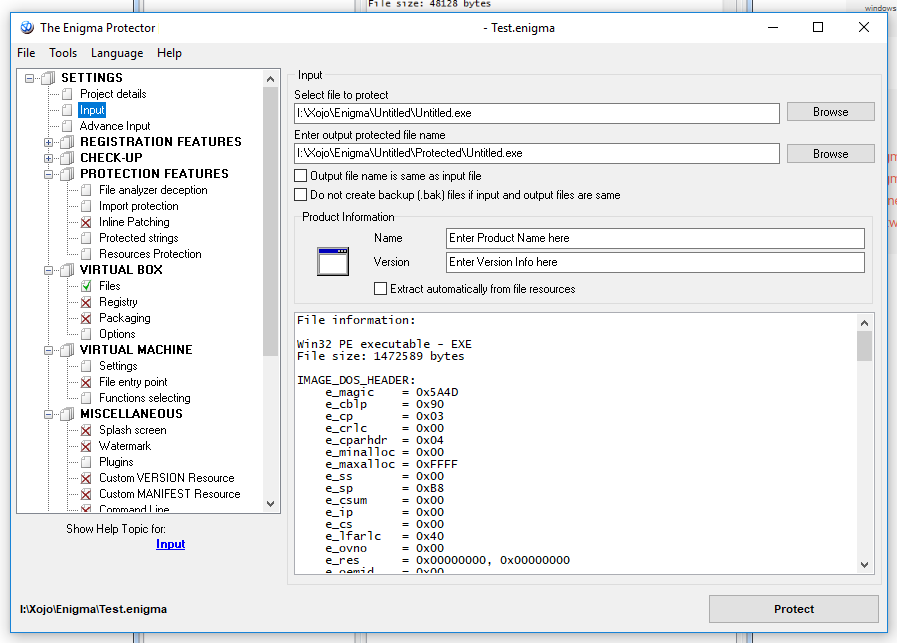 Then go to Virtual Box – Files panel and add the input file to the %DEFAULT FOLDER%
Then go to Virtual Box – Files panel and add the input file to the %DEFAULT FOLDER%
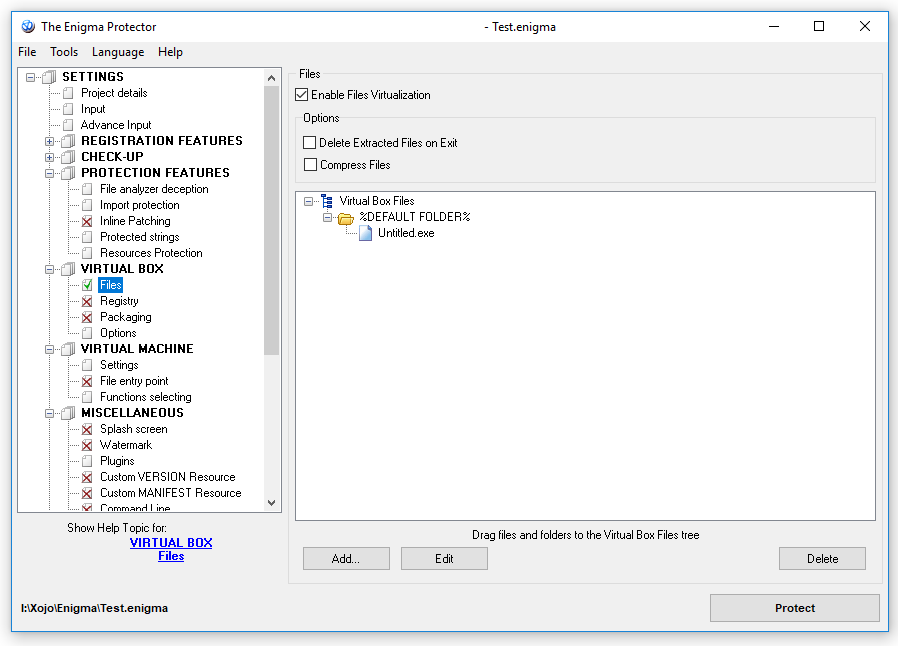
Try to protect the file now and run it. Make sure that the protected file works at this step (don’t forget to put Xojo runtime located at the folder “Untitled Libs” to the folder where protected executable is located). We could stop here and apply licensing or trial settings for protection, but this method has one major disadvantage – the original file is placed in Virtual Box and thus can be extracted by advanced cracker.
Merge Xojo runtime to single executable (aka, Advanced protection of Xojo files)
Copy the enigma_ide.dll from 32Bit-Xojo-Enigma-API-v1.0 or from the Enigma Protector 32 Bit Installation folder into “I:\Xojo\Enigma\Untitled\Untitled Libs” (in this example).
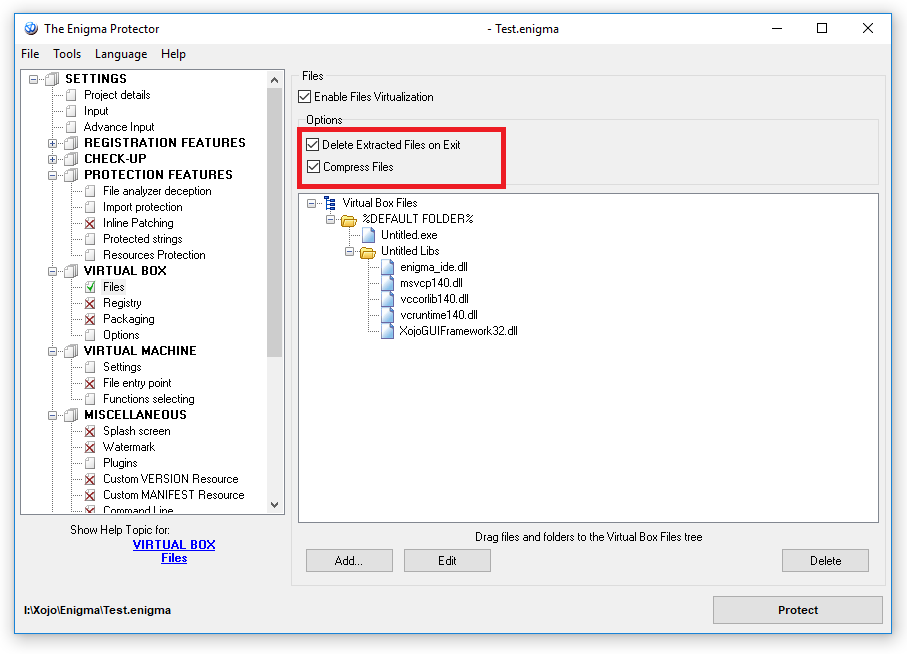
In Enigma Protector, go to Virtual Box -> Files panel enable it. Using drag and drop, put the “Untitled Libs” into %Default Folder% from Windows Explorer (or add files manually using Add… button)
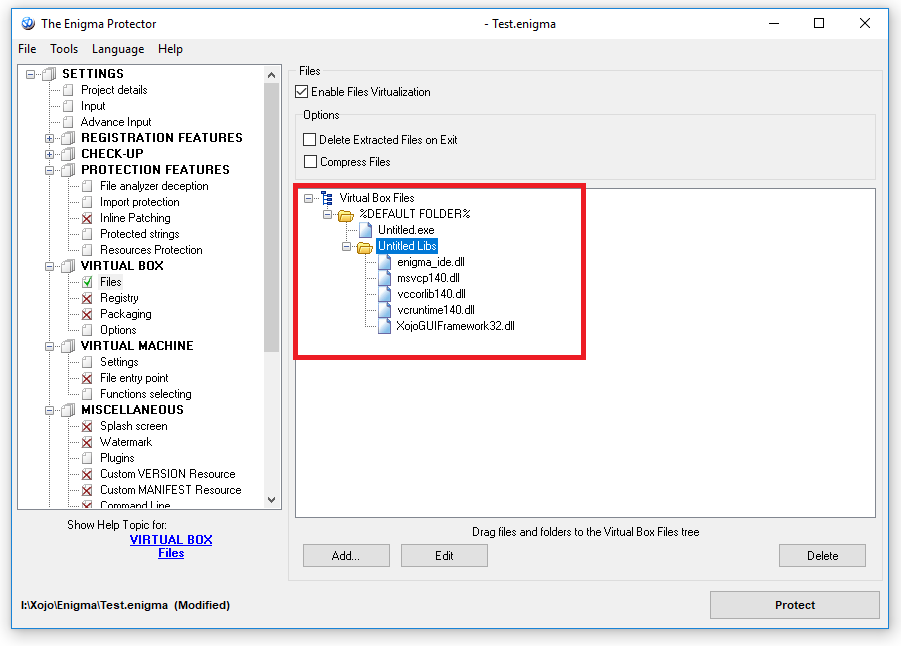 You may also want to enable files compression to make the protected file smaller
You may also want to enable files compression to make the protected file smaller
Since we have included all of the required runtime files into protected executable, it won’t need these files anymore (Enigma Protector will emulate these files in memory!), so you can delete “Untitled Libs” folder with files from the folder where protected executable located.
Now click “Protect” button and try to run the bundled executable file (“I:\Xojo\Enigma\Untitled\Protected\Untitled.exe”). If everything is going correctly, protected file should display the “Hardware ID” on the example app, like on our screenshot:
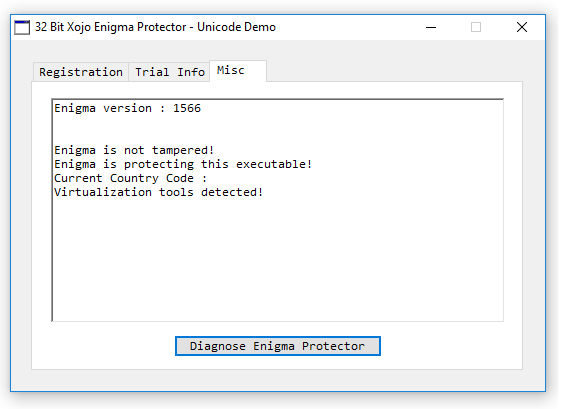
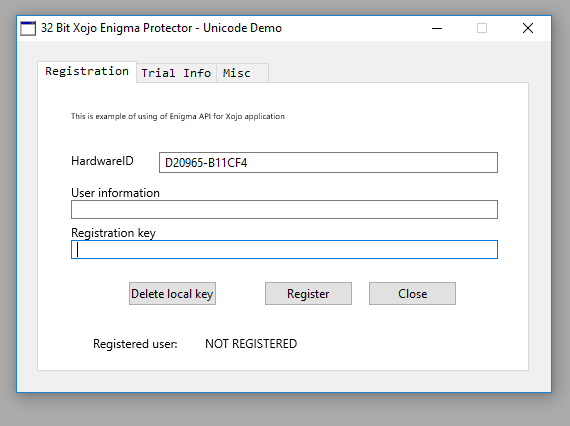 Go to “Misc” tab and click on “Diagnose Enigma Protector” :
Go to “Misc” tab and click on “Diagnose Enigma Protector” :
Congratulations! you’ve protected a Xojo example application using the Enigma Protector!
Common Protection Settings
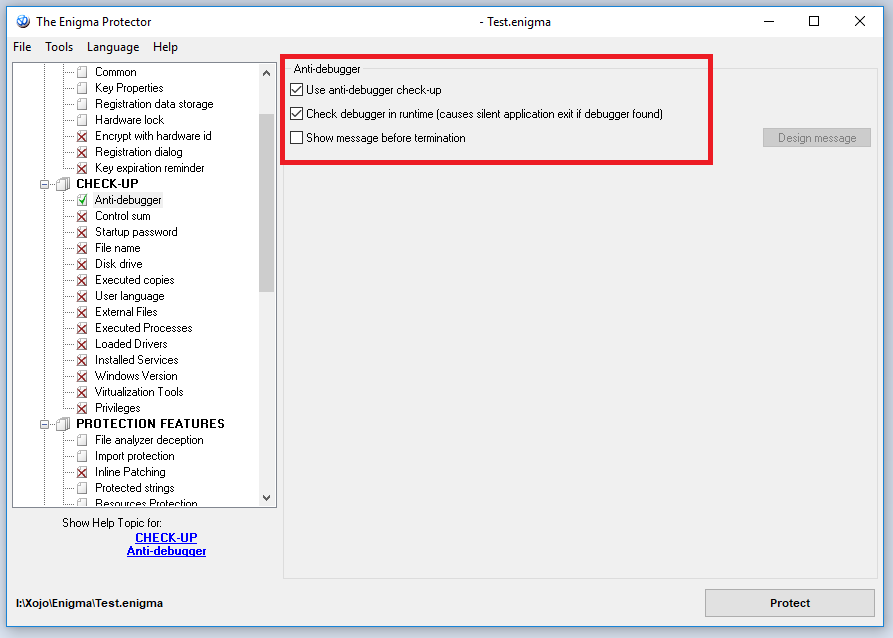
Go to Enigma Protector -> Check-Up -> Anti Debugger, checklist the “Use anti-debugger checkup“, and un-check “Show message before termination” and also checklist the “Check debugger in runtime“. These settings help to prevent attacker to debug your Xojo application on either Application startup or while the application already running and close application without any messages to confuse un-motivated attacker.
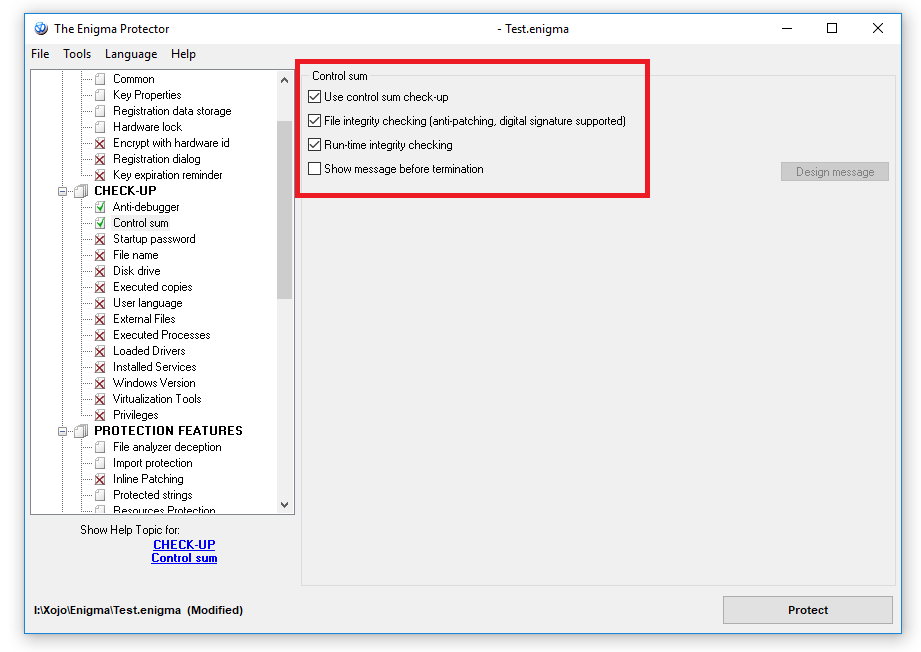
Next would be Check-Up->“Control Sum“, this is used, in general, to protect the protection and application core against being changed/patched. The optimal settings would be like these:
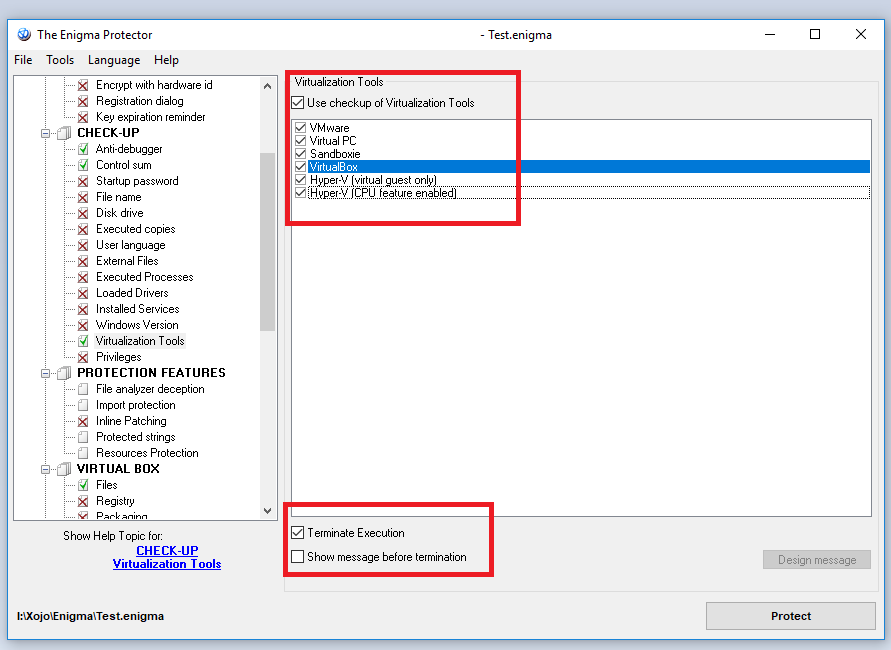
Furthemore, the next settings is Check-Up->Virtualization Tools, attacker commonly use virtualization tools such as Virtual Box, VMWare to attack, debug and crack the application, so by using this Check-Up we can detect the most common virtualization tools and exit silently:
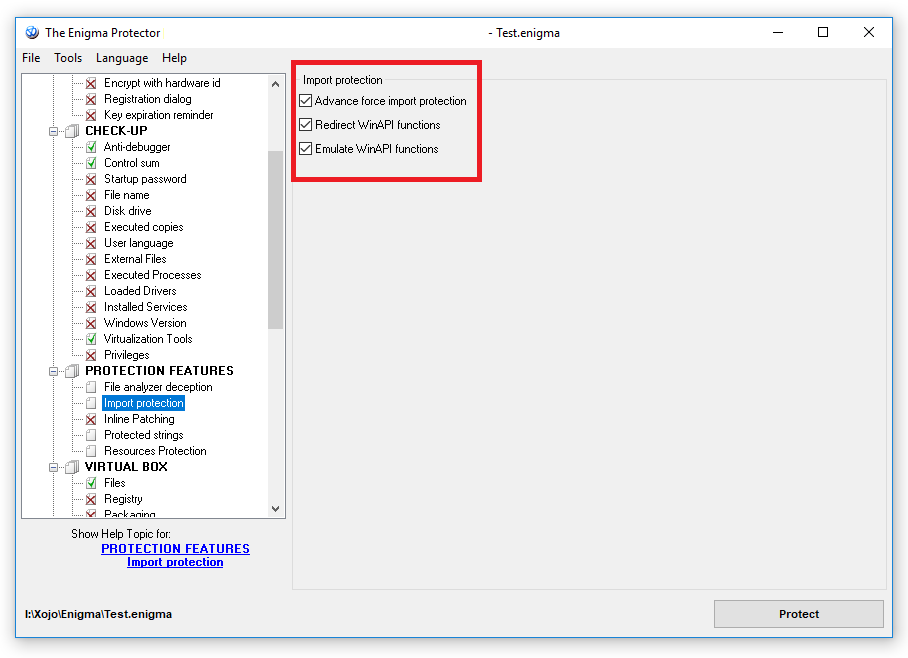
 The next would be, PROTECTION FEATURES->Import Protection:
The next would be, PROTECTION FEATURES->Import Protection:
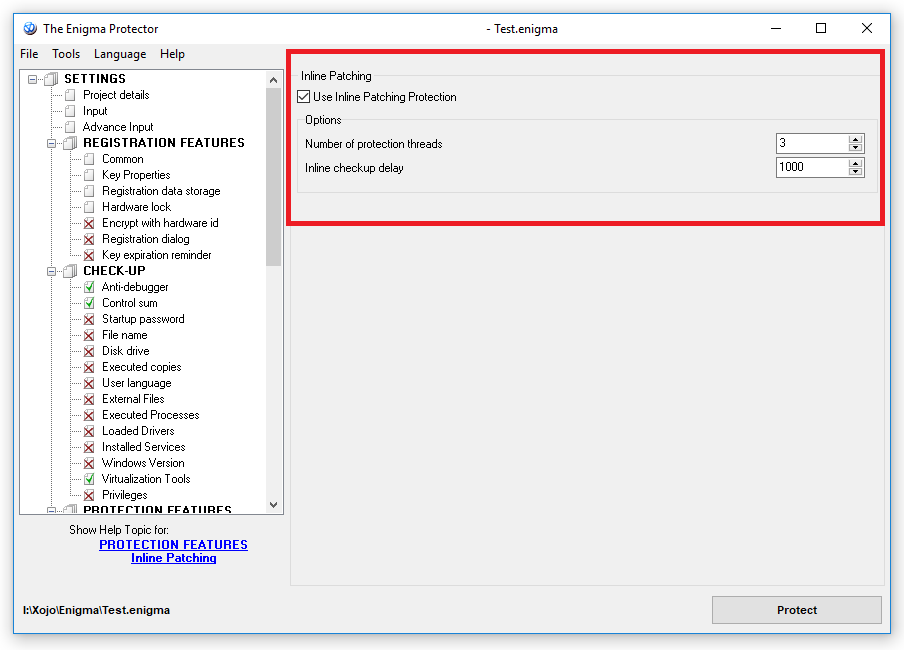
 Last but not least for the recommended common protection settings is PROTECTION FEATURES->Inline Patching, this is to prevent on the fly application patching for being used, or most commonly known as “loader” crack, recommended setting is the default one would be enough as ths check is computer’s resources sensitive:
Last but not least for the recommended common protection settings is PROTECTION FEATURES->Inline Patching, this is to prevent on the fly application patching for being used, or most commonly known as “loader” crack, recommended setting is the default one would be enough as ths check is computer’s resources sensitive:
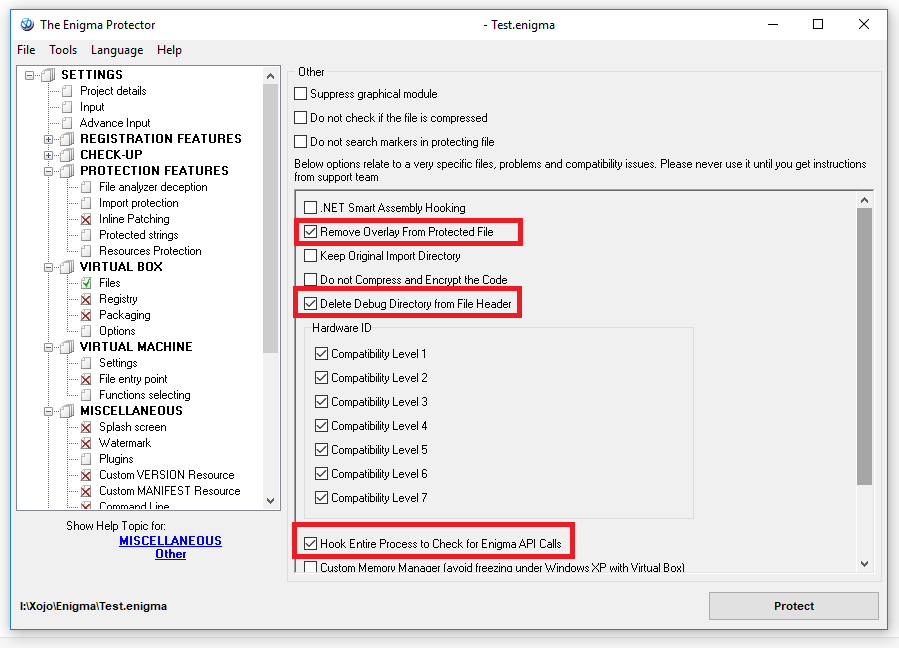
Since protection application reads overlay data from the virtual file (the original exe that we included into Virtual Box), we do not need an overlay in the original file anymore. To remove overlay from the protected file, use the option Miscellaneous – Other – Remove Overlay from Protected File, Don’t forget to also check “Hook Entire Process to Check for Enigma API Calls”
Note: Those are only the recommended protection settings that are commonly used by most protected applications, please be careful with protection settings as they can lead slow application load.
Licensing settings
Licensing settings can be used if you wish to sell your application and/or limit it’s usage to particular persons only. I.e. if you wish the application to require the license key before start or while it is working.
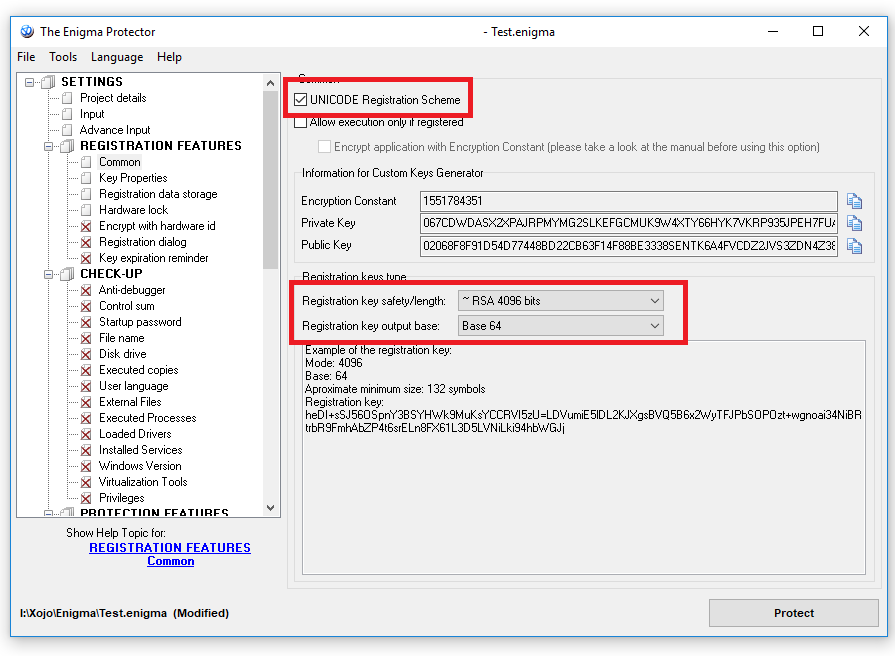
In Enigma Protector go to “REGISTRATION FEATURES“ -> Common, check the “UNICODE Registration Scheme” if most of your users have Unicode characters on their names.
On the registration key safety/length you could select either the license key will be safer either shorter, we recommend it to be safer, so pick “~RSA 4096 bits“.
And pick the Registration key output base into “base 64” for shortest possible key.
The endpoint of out modifications should be like these:
Now on to “REGISTRATION FEATURES“ -> Registration data storage, the recommended settings are (please change the paths to own one, to avoid being overwritten, or just keep default settings there):
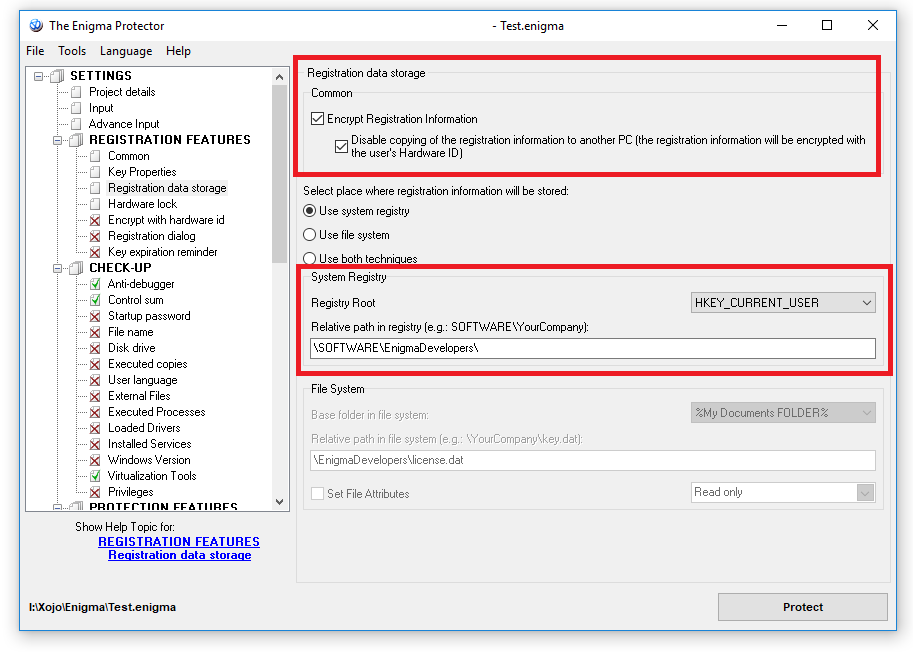 It’s recommended to change the default Relative path in registry and files.
It’s recommended to change the default Relative path in registry and files.
Trial settings for Xojo Application
Trial settings are different limitations that you could embed to protected application to force user to obtain/purchase the license key for application to get rid of these limitations. So, trial limitations are working until the application is not registered with valid license key. Once protection finds a valid license key, trial limitations stop to work. If this does not fit in scenario of your application, just skip this section.
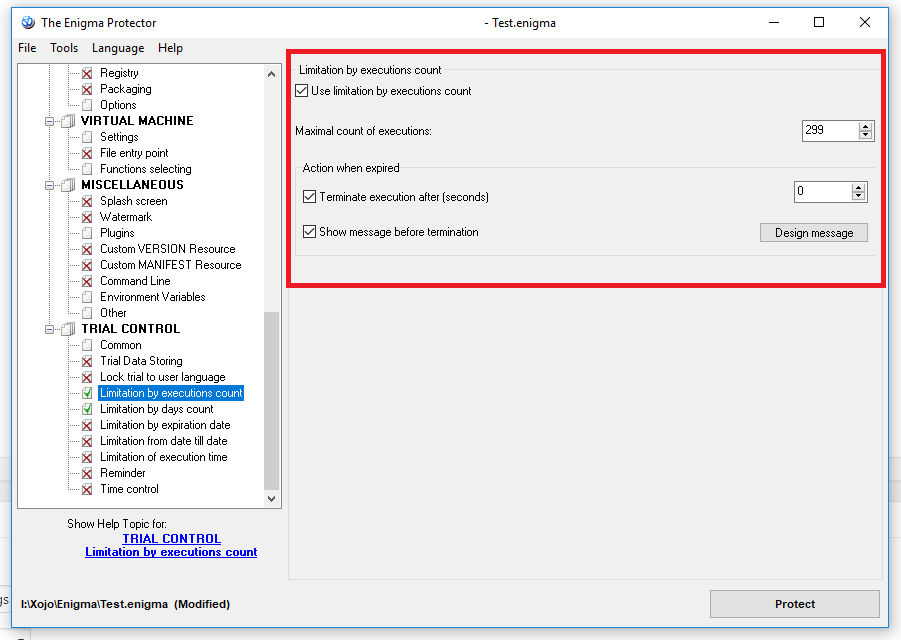
Go to TRIAL CONTROL->Limitation by Execution Counts:
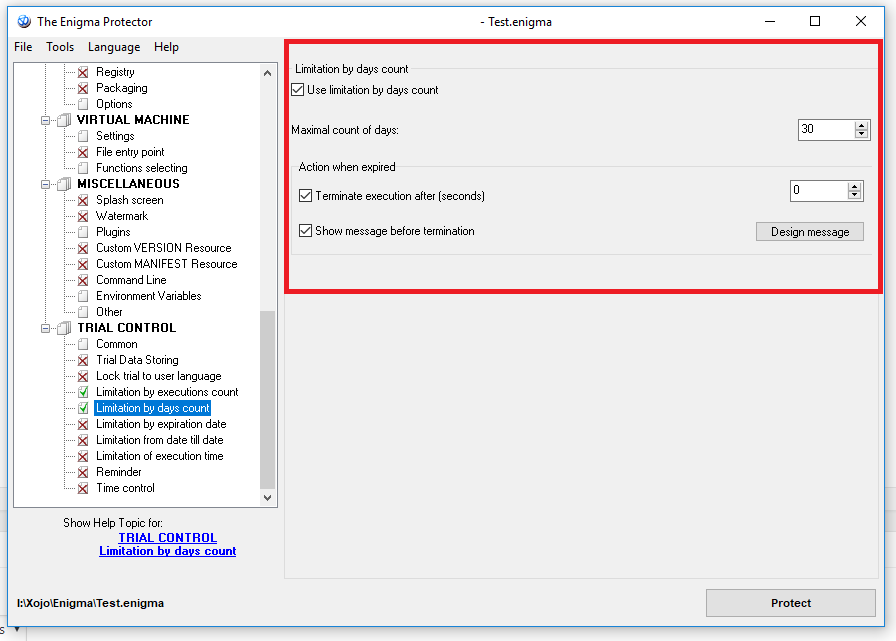
TRIAL CONTROL->Limitation by Days Counts:
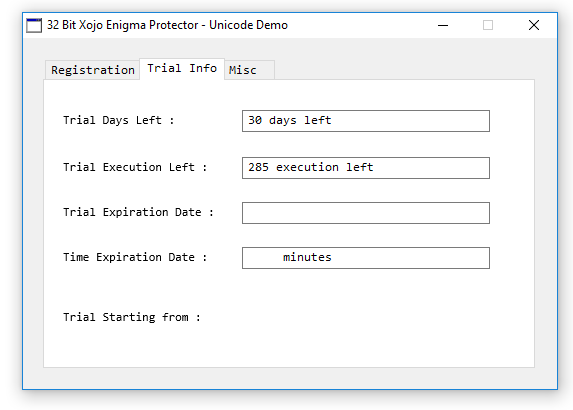
 Save the Enigma Protector project, and click “Protect”, and run the “I:\Xojo\Enigma\Untitled\Protected\Untitled.exe”. In the protected Xojo application, go to “Trial Info” tab, the trial info should show the protection status:
Save the Enigma Protector project, and click “Protect”, and run the “I:\Xojo\Enigma\Untitled\Protected\Untitled.exe”. In the protected Xojo application, go to “Trial Info” tab, the trial info should show the protection status:
 There are various types of trial for applications, it depends on your own bussiness model and how are you planing to use and sell the app.
There are various types of trial for applications, it depends on your own bussiness model and how are you planing to use and sell the app.
Registering the Application
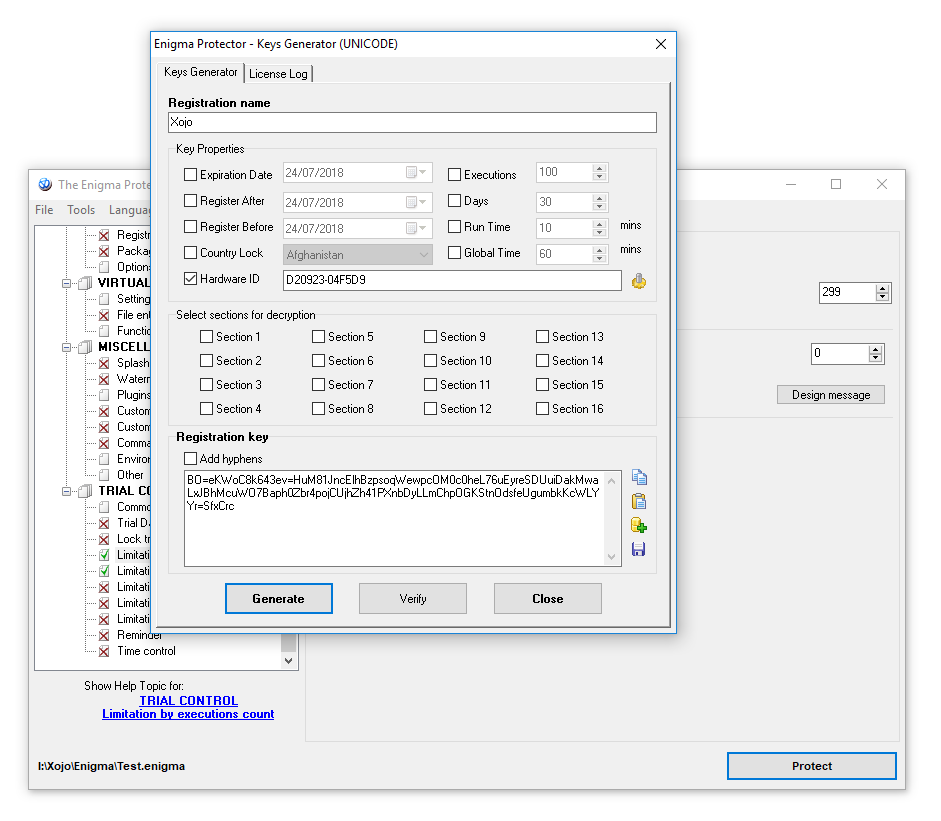
Now let’s register our Xojo example application with license key. In the Enigma Protector, click on menu “Tools->Key Generator“, enter “Xojo” as our “Registration name“.
Check the “Hardware ID“, and copy the Hardware ID from the protected application. Click “Generate” to create a license key.
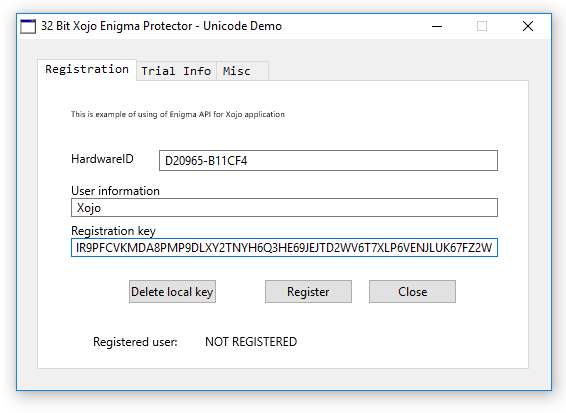
 Copy/paste the registration information from the Key Generator into our running Xojo example application:
Copy/paste the registration information from the Key Generator into our running Xojo example application:
 And click “Register”, if everything goes right, it will display a dialog box with message “Thanks for registration”.
And click “Register”, if everything goes right, it will display a dialog box with message “Thanks for registration”.
We also adopted the Enigma SDK for 64 bit Xojo, please download it there 64Bit-Xojo-Enigma-API-v1.0
In this article we described some, but not all, of the features of Enigma Protector. Enigma Protector is really more flexible and powerful than we described there. If you have confusions with something, have questions or ideas for improvements, please send us email at support@enigmaprotector.com