Delphi (Lazarus, FreePascal) applications are most suitable for protection with Enigma Protector. Here we discuss about protection of native Windows applications only (including Executable files, Dynamic Link Libraries, ActiveX (OCX) components, Services etc), 32 and 64 bit files.
Simple Protection
This is the basic protection with almost no protection features enabled. This case is not recommended to use, since it applies only “surface” protection, but anyway it works good for native files and could be enough for most of the cases.
- Select the file to protect
- Enter Product Name and Version information, this is important
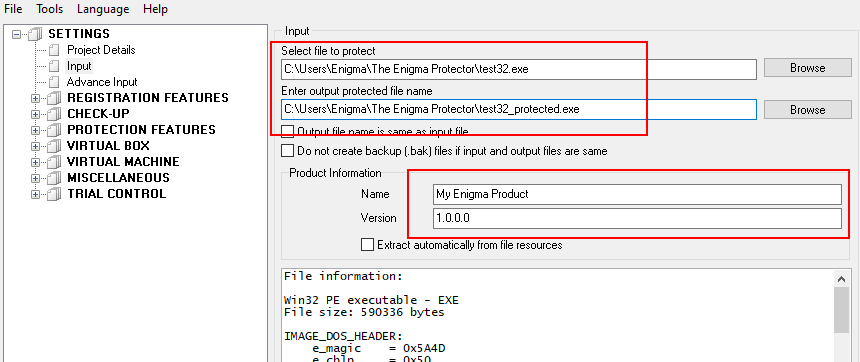
- Click Protect button. Once the protection process finishes, try protected file, it has to work same as non protected. Protected file size may increase, if the source file is small, or decrease, if source file is rather big.
Additional Protection Options
Here we apply additional protection options that could be useful for protection and do not require additional effort from developer or changes to application source code. These option can be used for almost all applications since they are very common for software protection.
- Checkup – Anti-debugger – protects application from being analyzed with, so called, “Debuggers”, special tools that allows to analyze how application is working, view machine code, change the execution behavior. Enigma Protector checks if debugger exists when the application is being loaded, since this is most critical moment that needs to be well protected, if you need to check for debugger always, when application is working, then the option “Check debugger in runtime” should be used. But if this option is used, please keep in mind that protection may terminate application when debugger is found automatically, without ability for user to save the work he/she done in your application.
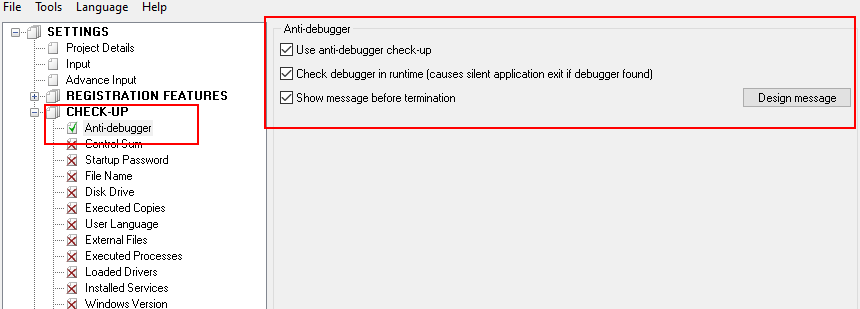
Checkup – Anti-debugger feature may not be suitable for developers, who produce software components that can be used in 3rd applications, since developers of 3rd software may use debuggers embedded into development IDE (like debuggers in Visual Studio) while development and tracing, this case protection will detect such kind of debugging tools too.
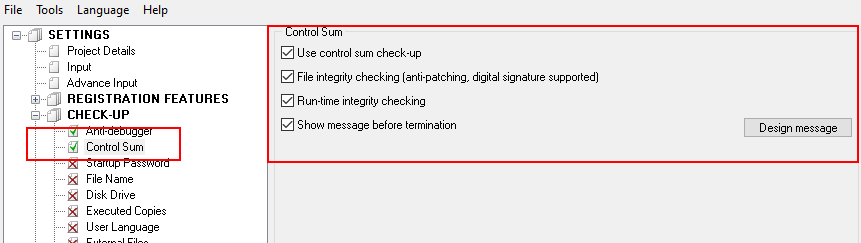
- Checkup – Control Sum – feature detects the changes of protected file and protection core in memory. It is recommended to be enabled, unless protected file can be somehow changed after protection (except Code Signing, which is compatible with current feature).
- Protection Features – Import Protection – specific options to protect Import Directory of PE file, which is often used by cracker to analyze protected file.
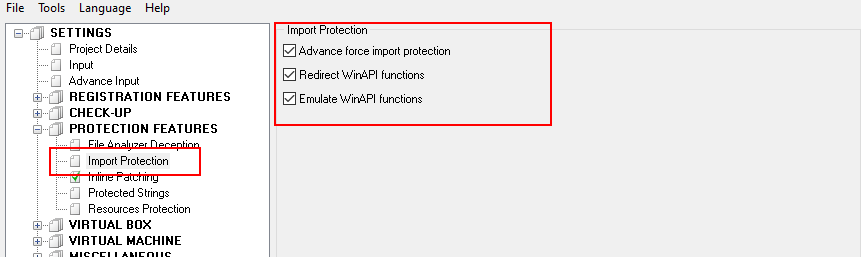
Protection Features – Import Protection may not be compatible with some .dll files that are used for injection to another process. If you use Enigma Protector to protect such kind of .dll files, these options should all be unchecked.
- Protection Features – Inline Patching – this feature monitors changes of the memory that belongs to application or protection. Protection memory should not be modified at all, but application memory, in some cases could be modified by different components. This feature worth to use, however you need to carefully check if your application is suitable with it.
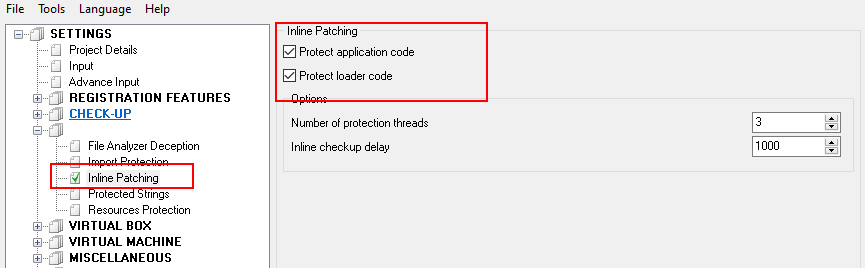
- Virtual Box – Files – famous feature that allows to merge files of your application into protected .exe, after protection you do not need to have embedded files on the disk anymore, they will be emulated in memory by protection. If your application contains from multiple files, specially different .dll files, it is recommended to use Virtual Box to merge them, hide from user and protect from being extracted or modified.
Virtual Box – Files is not compatible with device drivers files. Such files should be excluded from protection. Also, Virtual Box does not save changes to virtual files if application makes it (after restart, all changes made to virtual files are gone, this relates to Enigma Protector version up to 7.1).
Virtual Machine
Virtual Machine is the most powerful and modern techniques for protection of application code. Each application contains a code which exists in process memory and executed by the system, this code can be viewed by cracker, reversed (to understand the code logic), changed, and so cracked. If you need to protect some part of code from being viewed or changed then Virtual Machine should be applied to such code.
Why it is impossible to protect all the code with Virtual Machine? Code, protected with virtual machine becomes bigger and much slower than original. Protecting whole application code with virtual machine makes it impossible to use such file. Virtual Machine should be used carefully for high loaded parts of code, since the execution speed will be much decreased.
We provide two ways how to apply virtual machine – through Enigma Protector interface (with help of MAP file) and through the markers injected into source code.
Let’s check the first way, it requires less attention from developer. Select the file to protect and go to Virtual Machine – Functions Selecting. Here you need to Add Functions to protection. Usually, the functions selecting dialog will be shown as following, there is only one available function to add – EntryPoint
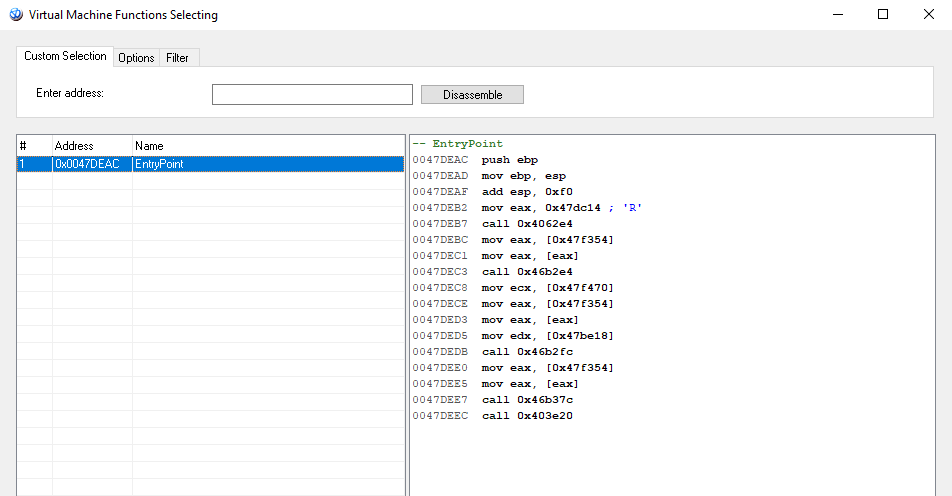
Starting from version 7.1 Enigma Protector supports browsing through the code (double click on “call” or “jmp” instruction in disassembler view) and entering custom address to disassemble and add to virtual machine (switch to Custom Selection tab at the top of the dialog and enter custom address to disassemble).
Since there are no much options to select, we recommend to compile a MAP file in Delphi/Lazarus IDE which helps to select more functions in Virtual Machine. MAP file contains definitions of function names and addresses inside compiled file (this information is not embedding into compiled file, thus we force compiler to keep this information for us in MAP file). For Delphi it can be specified in project options, following feature

for Lazarus, the following custom option to generate MAP file can be used
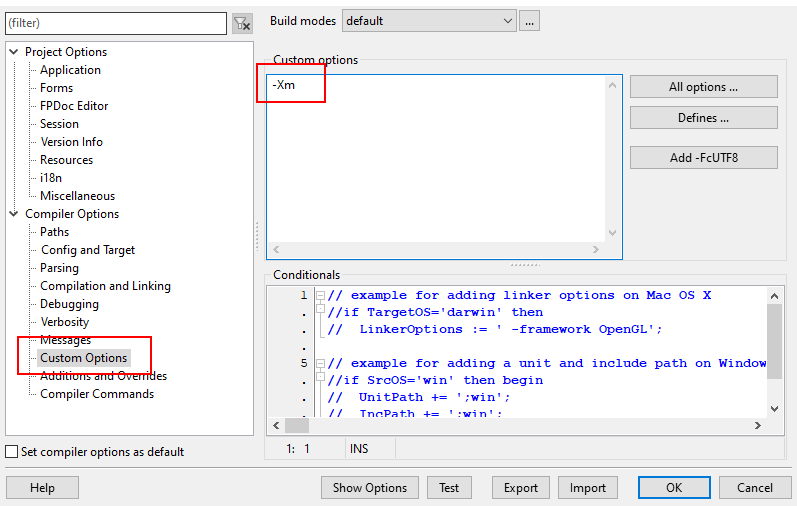
When MAP file is generated, it has (should have, otherwise Enigma Protector does not find it) the same file name as file to protect, but with .map extension.
Please check how functions selecting dialog changes, when .map file is used. There are a lot of functions available to select and function names in the disassemble view
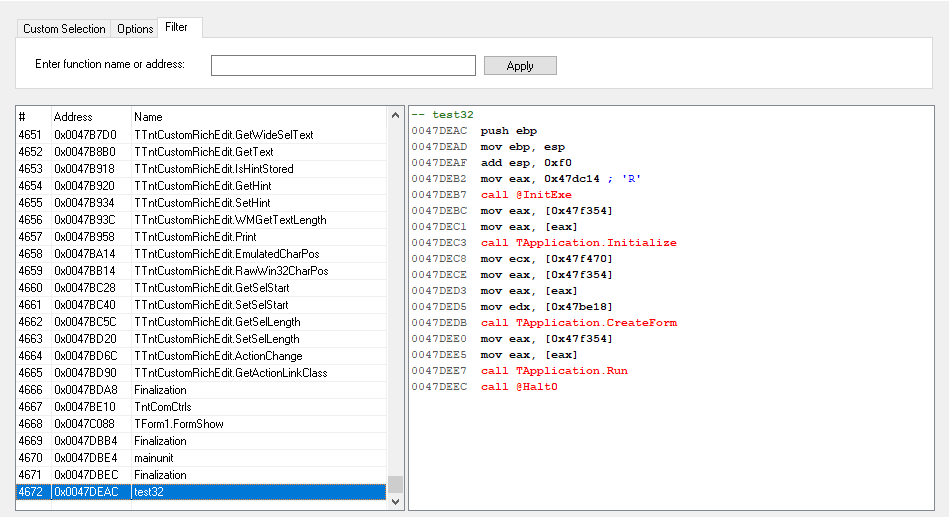
When adding a function, under Options menu you can select the virtual machine type which will be applied to selected functions, it can be either RISC either Classic. Virtual Machine type can also be changed in the Virtual Machine – Functions Selecting panel in Enigma Protector.
Classic virtual machine – enough small and fast. More functions can be selected for virtualization with it, without much affect on execution speed and file size. But it also easier to reverse by the cracker.
RISC virtual machine – heavy and slow, recommend to apply it to few most critical functions only. But it is rather safe, difficult to reverse and analyze.
Applying virtual machine with markers through application code requires changes to it, re-compilation of application, so this way is not suitable if you can’t change the source code.
The way how to embed code markers in source code are different for x86 and x64 version (matches version 7.1 of Enigma Protector, planned to be fixed in next releases).
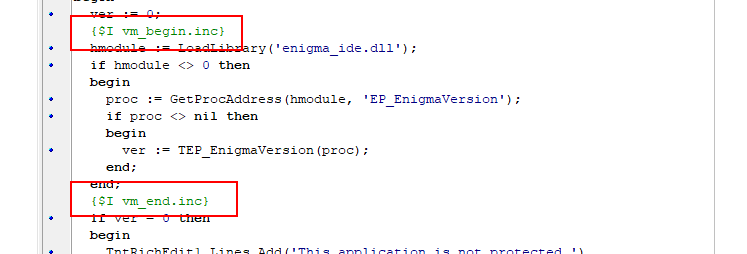
For x86 version it can be done using .inc files that you may find inside “EnigmaSDK\Delphi\” folder of installed Enigma Protector. We are interesting in files vm_begin.inc/vm_end.inc and
vm_risc_begin.inc/vm_risc_end.inc files.
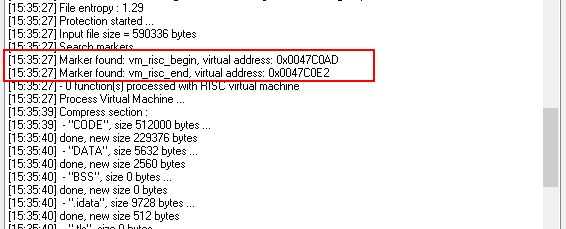
So, to protect the code with Classic virtual machine, quote this code with vm_begin.inc and vm_end.inc include files, like that
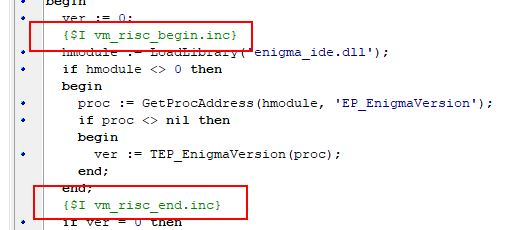
For protection with RISC virtual machine, vm_risc markers can be used
For x64 files Delphi/Lazarus should include the unit Enigma_IDE.pas into project and use EP_Marker function to quote the code for protection, like this
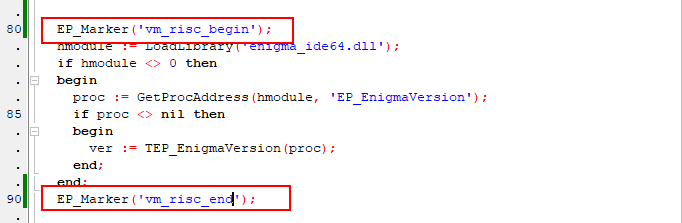
After compilation and protection, make sure Enigma Protector found markers in application and did not produce any warnings or errors.
Enigma API
Enigma API is a set of functions that allows application to communicate with protection, extract protection status, parameters and so on. Enigma API functions defined for different programming languages in EnigmaSDK folder of installed Enigma Protector. Delphi/Lazarus files have to use files from “EnigmaSDK/Delphi” folder, the file enigma_ide.pas should be added into project and then included in necessary unit through uses statement.
Examples, of Enigma API usages can be found inside “Examples” folder.
Why using Enigma API functions makes the protection stronger? Enigma API allows integration of protection inside application, so for cracker, to get rid of protection, it will be necessary to remove all the parts of code where Enigma API are used and also trace if Enigma API results do not affect execution of the file.
We will talk just some of Enigma API functions here which are not tied to licensing or trial features, just few functions that can be used for any application independent on protection needs.
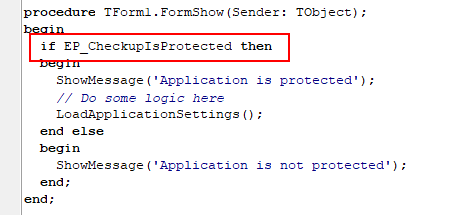
EP_CheckupIsProtection function returns true if application is protected. If protection will be somehow gone, call of function will either fail, either cause crash. So it can be used to perform some important logic, based on the result that function returns
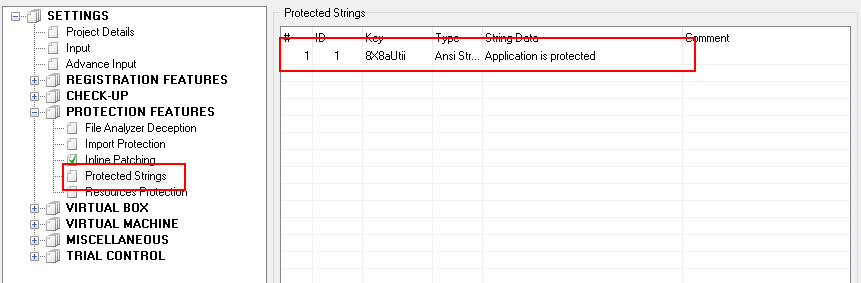
Protected strings functionality can be used to improve the code above. This feature can be used for any application, since it is suitable for most of the cases. To use protected strings, we first need to specify the string in Enigma Protector interface, like that
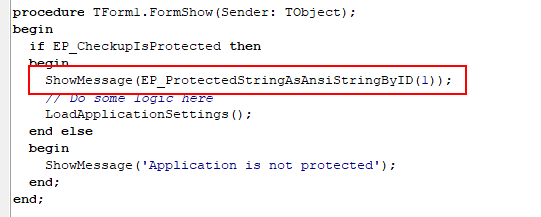
Then, extract it from protection using Enigma API function EP_ProtectedStringAsAnsiStringByID
Please note,
EP_ProtectedStringAsAnsiStringByID is just a wrapper under native EP_ProtectedStringByID function, while looks as following
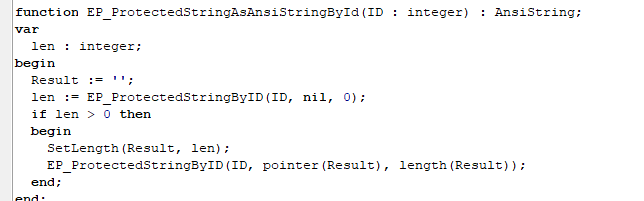
What protection the protected strings feature does? It stores embedded strings inside protection, application communicates with protection to extact these strings. If cracker removes protection, application won’t be able to call Enigma API functions, won’t be able to get protected strings, so it won’t work at all.
